There are many applications of BPF:
Allowing non-root, user-customizable firewall:
https://sweetness.hmmz.org/2015-07-25-fun-with-bpf-or-shutting-down-a-tcp-listening.html
"It is a rare situation where decades of undisciplined tinkering with Linux esoterica occasionally pay out, but this was such an occasion. Unlike in BSD, where Berkeley Packet Filter is implemented as a root-only device that attaches to entire network interfaces, on Linux it is implemented in terms of a socket optionthat usually attaches to AF_PACKET or AF_RAW sockets, however it is a little known fact you can also attach such filters to AF_INET sockets, and better yet, the ability to do so does not require root. Essentially, Linux allows non-root programs to configure their own little private firewall."
https://www.youtube.com/watch?v=apU5sg0Ui5U
Stracing and understanding the flow of syscalls + bpf() calls + argument: complimenting stracing via BPF?
https://blog.yadutaf.fr/2016/03/30/turn-any-syscall-into-event-introducing-ebpf-kernel-probes/
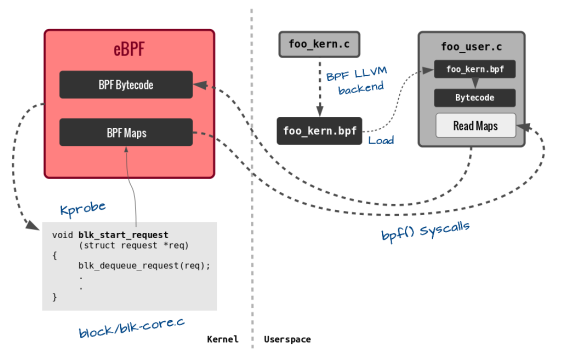
https://suchakra.wordpress.com/2017/05/23/an-entertaining-ebpf-xdp-adventure/ (archtiecture of Netroname smart NIC)
https://lwn.net/Articles/719850/
https://cilium.io/blog/2018/04/17/why-is-the-kernel-community-replacing-iptables/
Kernel Path understanding and tracing:
https://developers.redhat.com/blog/2018/12/03/network-debugging-with-ebpf/ (Network debugging)
https://elinux.org/images/d/dc/Kernel-Analysis-Using-eBPF-Daniel-Thompson-Linaro.pdf (Kernel analysis)
https://www.ntop.org/wp-content/uploads/2018/10/Sabella.pdf (network traffic analysis)
Network packet analysis and processing (with speed):
https://blog.cloudflare.com/epbf_sockets_hop_distance/
https://www.youtube.com/watch?v=apU5sg0Ui5U
https://www.netronome.com/blog/bpf-ebpf-xdp-and-bpfilter-what-are-these-things-and-what-do-they-mean-enterprise/ https://lwn.net/Articles/747551/ https://cilium.io/blog/2018/04/17/why-is-the-kernel-community-replacing-iptables/
https://forum.openwrt.org/t/what-is-the-difference-between-nftables-and-bpfilter/24602
Performance Analysis:
https://www.memsql.com/blog/bpf-linux-performance/
AppSwtich:
https://suchakra.wordpress.com/2018/03/31/so-whats-this-appswitch-thing-going-around/
https://jpetazzo.github.io/2018/03/13/appswitch-hyperlay-network-stack-future/
https://hub.docker.com/r/appswitch/ax/
Containers analysis:
https://kubernetes.io/blog/2017/12/using-ebpf-in-kubernetes/
Intrusion Detection:
https://www.slideshare.net/AlexMaestretti/security-monitoring-with-ebpf
https://qmonnet.github.io/whirl-offload/2016/09/01/dive-into-bpf/
https://blog.sflow.com/2016/05/berkeley-packet-filter-bpf.html
https://www.netresec.com/?page=Blog&month=2015-11&post=BPF-is-your-Friend
Tracing – both network and processes:
http://www.brendangregg.com/blog/2018-10-08/dtrace-for-linux-2018.html
https://twitter.com/daniel_bilar/status/881570223840780289
https://www.usenix.org/legacy/events/vee05/full_papers/p153-yunhe.pdf
https://suchakra.wordpress.com/2015/05/18/bpf-internals-i/
https://www.iovisor.org/blog/2015/10/15/bpf-internals-ii
https://www.usenix.org/legacy/events/vee05/full_papers/p153-yunhe.pdf
https://www.youtube.com/watch?v=w8nFRoFJ6EQ
https://www.usenix.org/conference/atc17/program/presentation/gregg-superpowers
https://elixir.bootlin.com/linux/v4.14.8/source/kernel/trace/bpf_trace.c#L212
https://elixir.bootlin.com/linux/v4.20-rc1/source/kernel/trace/bpf_trace.c
What are all the technologies/foundation which BPF used:
bpf stacks: http://www.brendangregg.com/blog/2016-01-18/ebpf-stack-trace-hack.html
bpf output:
https://lwn.net/Articles/649965/
https://stackoverflow.com/questions/47914219/output-from-bpf-printk
bpf + kprobes:
https://lwn.net/Articles/636976/
https://elixir.bootlin.com/linux/v4.20/source/kernel/kprobes.c
https://lwn.net/Articles/132196/ (Intro to Kprobes)
https://www.kernel.org/doc/Documentation/kprobes.txt
https://github.com/weaveworks/tcptracer-bpf
https://www.ibm.com/developerworks/library/l-kprobes/index.html
https://vjordan.info/log/fpga/how-linux-kprobes-works.html
https://www.kernel.org/doc/Documentation/trace/kprobetrace.txt
bpf + tracepoints:
https://lwn.net/Articles/683504/
http://thread.gmane.org/gmane.linux.kernel.api/8127/focus=8165
bpf + userspace tracepoints:
https://lwn.net/Articles/753601/
bpf + systemtap:
https://developers.redhat.com/blog/2018/04/23/systemtaps-bpf-backend-tracepoint-support/
How to turn any syscall into an event: Introducing eBPF Kernel probes:
https://blog.yadutaf.fr/2016/03/30/turn-any-syscall-into-event-introducing-ebpf-kernel-probes/





















You must be logged in to post a comment.